Hi,
Maybe I am asking some strange questions here  but I am not a hash function pro…
but I am not a hash function pro…
I know hash functions in general are irreversible functions. Is the HMACHex() function reversible since it uses a secret key ? I would think it is not reversible because it uses also another algorithm like MD5 or SHA-256.
-
I would like to encrypt a column using HMACHex and then recover the original values. Is that possible in EasyMorph ?
-
In hmachex() we need to provide a “secret” key. We enter that key in EasyMorph either directly in the function or maybe via a parameter. How safe is that ? If one could get the EasyMorph file, he/she would have access to the secret key ?
-
Could we interpret the “key” in hmachex() as the ‘salt’ where a lot of security professionals are talking about when they are talking about a salted hash?
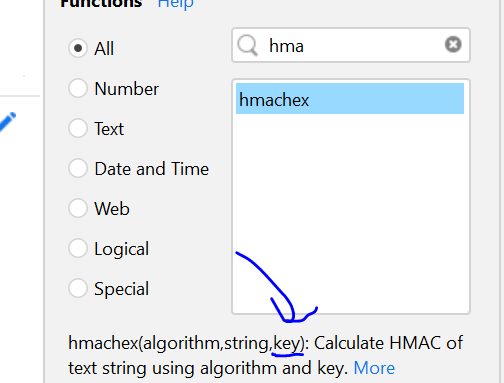
Remark: In the documentation online the arguments of the function are switched:
- Online: https://help.easymorph.com/doku.php?id=syntax:functions:hmachex it says: HMACHex(algorithm, key, text)
- In EasyMorph the “key” argrument is the third argument.
Thanks
Nikolaas