Hello @dgudkov, ok thanks for the information.
@olysak I have a three questions regarding the expiry of the the authorization codes for Salesforce / oAuth2 Process:
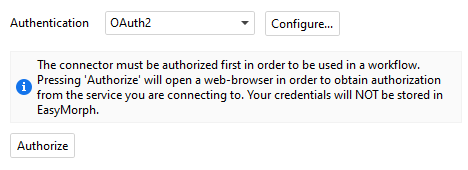
1. Expiry of link generated after pressing "Authorize"
In the following article (https://help.salesforce.com/s/articleView?id=sf.remoteaccess_oauth_web_server_flow.htm&type=5), it is mentioned that the authorization code expires after 15 minutes. However, we’re talking about the authorization code after the user has already authenticated.
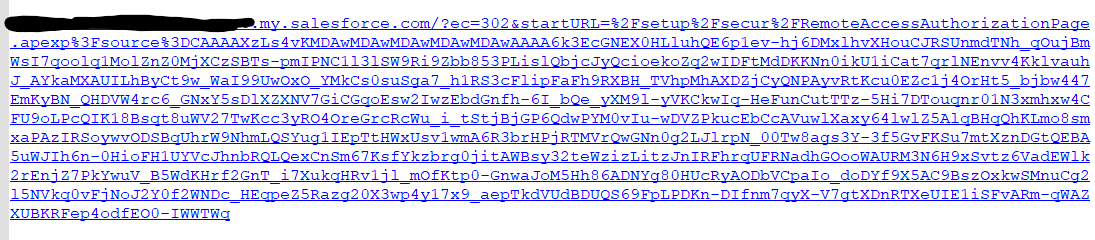
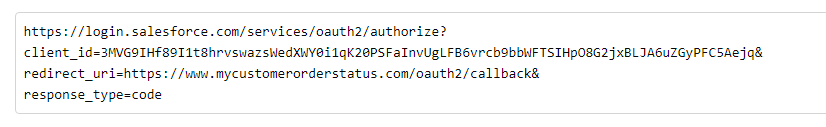
What about the link that EasyMorph generates when clicking on the “Authorize” button, that also includes a code? Here’s an example:
Does this link with a certain code (that changes every time I click on the authorize button) also expire? For now I’ve done a test of accessing this link 26 minutes after I pressed on the “Authorize” button, and I was able to log in and successfully authorize. I’m asking this because If I have to send this link to the clients for them to authorize, how long will these links work for? I know that I have 15 minutes to enter the authorization code once the user has authenticated (because Salesforce tells us this code expires after 15 minutes), but I don’t know about the link that is provided to get to the authorization page.
2. Format of link generated after pressing "Authorize"
On the other hand, why does this URL I just mentioned have this structure? It is different from
Is this because EasyMorph has already passed this to Salesforce when clicking “Authorize”, and the URL with the long code (screenshot before) is Salesforce’s response to that?
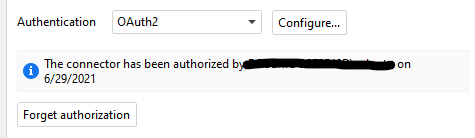
3. “State” parameter in final auth code URL
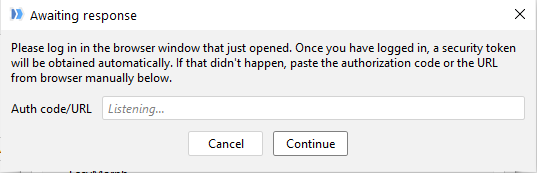
Finally I had a question regarding the URL with the final authorization code when the user has authenticated. It includes not only the authorization code (parameter “code”) but also parameter “state”. According to Salesforce, “state” is the following:
Is it something you send to Salesforce? Just wanted to understand how it worked. Is it necessary to also copy the “state” parameter into the following prompt, or only the “code” is necessary?
Thanks very much!!
Roberto